Latest Gear Live Videos
Australian iOS device users get held up for ransom

Posted by Ariel Levin-Waldman Categories: Apple, Smartphones, Mods / Hacks, Software,
You've probably heard it by now. There are no viruses on Apple products. They don't run .exe files. They don't get hacked. It's the reason I usually use my iPad to do my banking (that, and a lack of questionable browsing history.) I used to believe that.
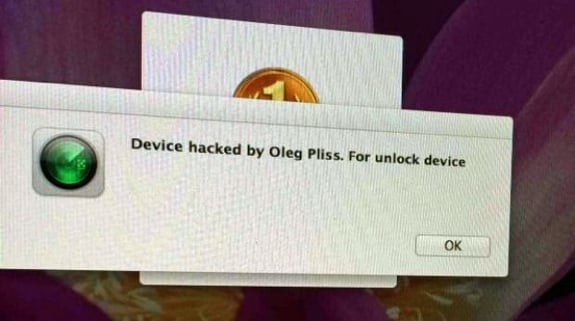
Well, now it looks like I have to confront the truth. In a series of cyber attacks that have swept Australia, iPhone users have been locked out of their devices and have received a message saying “Device hacked by Oleg Pliss. For unlock device, you need send voucher code by 100 usd/eur (Moneypack/Ukash/PaySafeCard) to email:lock404@hotmail.com for unlock."
According to Apple's support forums, the hack seems to operate through the “Find My Device” feature on Apple products, and it seems that the data may have been matched to an eBay breach that occurred earlier in the week.
People with a hacked device should immediately attempt to change their Apple ID credentials and set up multi-factor authentification.
Advertisement
Apple sets up Developer Center system status page

Posted by Jason Diaz Categories: Apple, Mods / Hacks,
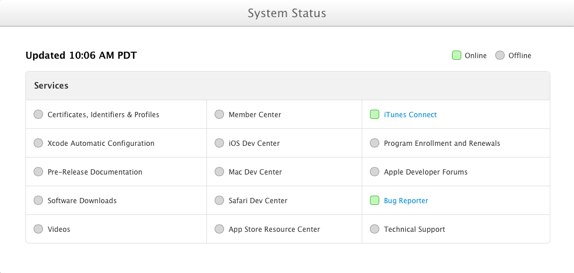
In light of last week's security breach by a security analyst, Apple has proactively introduced an online status page, much like the iCloud status page, but for the Developer Center. This status page allows registered Apple developers to track the progress as systems become available while Apple overhauls their backend services with added security. As you can observe there's still a lot of green missing. Here's a road map statement of their approach in bringing their services back online.
We plan to roll out our updated systems, starting with Certificates, Identifiers & Profiles, Apple Developer Forums, Bug Reporter, pre-release developer libraries, and videos first. Next, we will restore software downloads, so that the latest betas of iOS 7, Xcode 5, and OS X Mavericks will once again be available to program members. We'll then bring the remaining systems online. To keep you up to date on our progress, we've created a status page to display the availability of our systems. - Apple
Read More  | MacRumors
| MacRumors
Syrian Electronic Army strikes VoIP provider Viber

Posted by Jason Diaz Categories: Corporate News, Internet,

The Syrian Electronic Army strikes again at another VoIP provider, this time, Viber. We reported the cyber attacks on Tango, now it seems that the pro-Assad militant cyber group claims allegedly that it was able to download backups of Viber's database, which includes but it's not limited to phone numbers, device IDs and, supposedly, push notification tokens. Along with the purported intrusion, some Viber pages have been defaced. Viber has come forward and has stated that the intrusion is mostly harmless to customers of their VoIP services since they claim that the most vital user information is kept in a different database that can't be exploited by outsider threats. As always, Viber requests that 200,000 users be vigilant and report any suspicious activity with their accounts.
Today the Viber Support site was defaced after a Viber employee unfortunately fell victim to an email phishing attack. The phishing attack allowed access to two minor systems: a customer support panel and a support administration system. Information from one of these systems was posted on the defaced page.
It is very important to emphasize that no sensitive user data was exposed and that Viber’s databases were not “hacked”. Sensitive, private user information is kept in a secure system that cannot be accessed through this type of attack and is not part of our support system.
We take this incident very seriously and we are working right now to return the support site to full service for our users. Additionally, we want to assure all of our users that we are reviewing all of our policies to make sure that no such incident is repeated in the future. - Viber
Read More  | Arstechnica
| Arstechnica
Tango Messenger user info hacked by Syrian Electronic Army

Posted by Jason Diaz Categories: Software,

The Syrian Electronic Army (SEA) has come forward claiming that it has stolen millions of user email addresses, phone numbers and contact information of the popular video messaging service Tango. The 1.5 terabyte worth of compromised data has been confirmed by Tango on Twitter.
SEA has stated that it will hand over the information to its country's government lead by embattled President Bashir al-Assad. The compromise was possible due to an outdated WordPress installation.
Traditional telecommunication is to be avoided due to current war in Syria that has resulted in the rising death toll of over 100,000 lives. Thus, popular messaging services with VoIP capabilities are very popular in that part of world. So, it comes to no surprise that the exploit is for the sole purpose of monitoring, stamping out and finding rebel forces and sympathizers.
"Tango experienced a cyber intrusion that resulted in unauthorized access to some data. We are working on increasing our security systems. We sincerely apologize for any inconvenience this breach may have caused our members." -Tango
Read More  | Syrian Electric Army
| Syrian Electric Army
Apple Developer Portal hacked, security researcher responsible comes forward

Posted by Jason Diaz Categories: Apple, Corporate News,
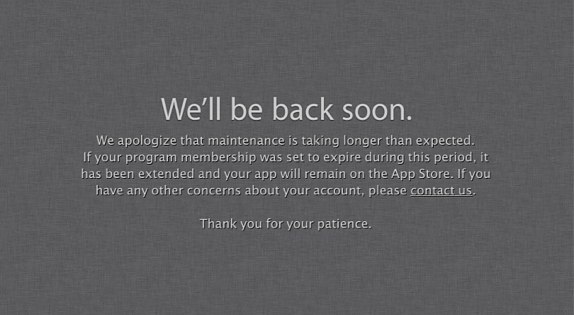
The Apple Developer Center portal has been in hiatus since last Thurday. Reasons for it being down took many by surprise as they were led to be believe it was related to a mundane web maintenance. However, Apple has come forward with information that the Dev site was compromised. Now, a security researcher named Ibrahim Balic has come forward claiming responsibility for the exploit several hours before the Dev site went into full lockdown.
Balic managed to see and copy Apple developer's full names and corresponding Apple ID and emails with an unavoidable injection tool attack. No other information was garnered from the exploit such as credit card information or App codes. Such information is under additional lock and key encryption housed in other servers.
Balic claims that he was also able to get a hold of the Apple ID of regular users. He stresses that this is for security research purposes only and he does not intend to give out any information to the general public as to how he managed the exploit. Full Apple statement below. Still, no apologies from Apple over the faux linen landing page. Here's a video of Balic discribing vulnerabilities within Apple's web services.
Read More  | AllThingsD
| AllThingsD
SIM card encryption hack found in millions of mobile phones

Posted by Jason Diaz Categories: Smartphones, Mods / Hacks,

A SIM card vulnerability has been uncovered in the encryption used in millions of phones that could allow hackers to send spoof texts. These texts would execute nefarious software that enables them the ability to listen in on calls, as well as read and send text messages, all within a couple of minutes. It could even copy your SIM card.
Cryptographer Karten Nohl and his security team has estimated that 750 million phones in circulation today are using an old 56-Bit DES encryption standard used in SIM cards that can be exploited. Nohl will present his findings at the annual BlackHat security conference held in Los Vegas. It is estimated that 25% of 1000 SIM cards tested in North America and Europe were vulnerable to the exploit.
In addition, it has been reported that Nohl has fully disclosed his findings to the GSM association, and that they have notified carriers and SIM venders of who exactly can be exploited. Nohl suggested that older obsolete systems should be replaced with new triple-based DES encryption.
Read More  | PCMag
| PCMag
Jailbreak your iOS 6 iPhone 5, iPad 4, iPad mini and more with evasi0n

Posted by Andru Edwards Categories: Apple, Smartphones, Handhelds, Mods / Hacks, Software,
The Evade3rs dev team has just released the first untethered jailbreak for the latest release of iOS, including devices that house an A6 or A6X processor. This means that owners of the iPhone 5, the iPad mini, and the 4th generation iPad can get in on the untethered jailbreak game. This means that you no longer need to connect to a computer each time you need to restart your device in order to maintain your jailbreak. That is good news!
Click to continue reading Jailbreak your iOS 6 iPhone 5, iPad 4, iPad mini and more with evasi0n
Hacker shows how to get free iOS in-app purchase content in major Apple security breach (video)

Posted by Andru Edwards Categories: Apple, Corporate News, Mods / Hacks, Software,
A Russian hacker has uncovered a serious breach in Apple's iOS App Store in-app purchase model that allows anyone to get access to pretty much any in-app purchase content completely for free. Surprisingly easy to set up, the model just requires the installation of two security certificates, followed by you entering a different DNS server in your Settings app on your iPhone, iPad, or iPod touch. That's it.
Read More  | In-Appstore via 9to5Mac
| In-Appstore via 9to5Mac
How to draw a perfect circle without any tools

Posted by Andru Edwards Categories: Design, Videos,

If you draw anything like we do, attempting to put the pencil to paper to form a circle usually turns out in some sort of watermelon-shaped disaster. Until now. The video below offers a piece of advice that should allow anyone with at least two fingers to draw a perfect circle. It's actually pretty ingenius, really. You simply use one finger as the center point, and place the pencil on the paper similar to a compass. From there, you just rotate the page itself, rather than having to move your hand. Check the video to see how it's done.
[Photo: BigStockPhoto]
Click to continue reading How to draw a perfect circle without any tools
Jailbreak your iOS 5.1.1 iPhone 4S, new iPad, and more with Absinthe 2.0

Posted by Andru Edwards Categories: Apple, Smartphones, Handhelds, Mods / Hacks, Software,

The Chronic Dev Team has just released the first untethered jailbreak for the latest iOS devices that house an A5 or A5X processor. This means that owners of the iPhone 4S, the new iPad (2012), and the iPad 2 can get in on the untethered jailbreak game. This means that you no longer need to connect to a computer each time you need to restart your device in order to maintain your jailbreak. That is good news!
Click to continue reading Jailbreak your iOS 5.1.1 iPhone 4S, new iPad, and more with Absinthe 2.0